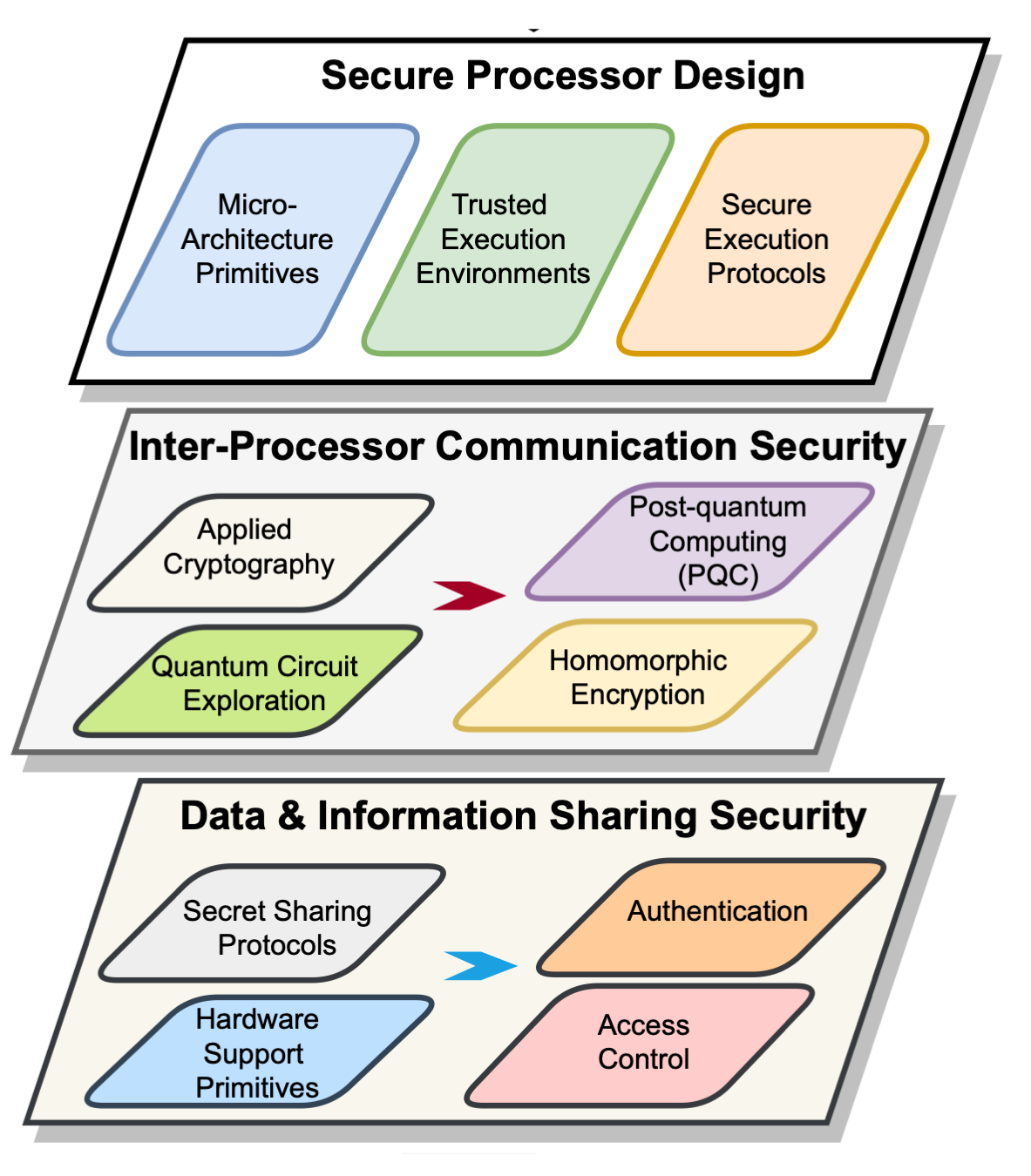
Research Projects
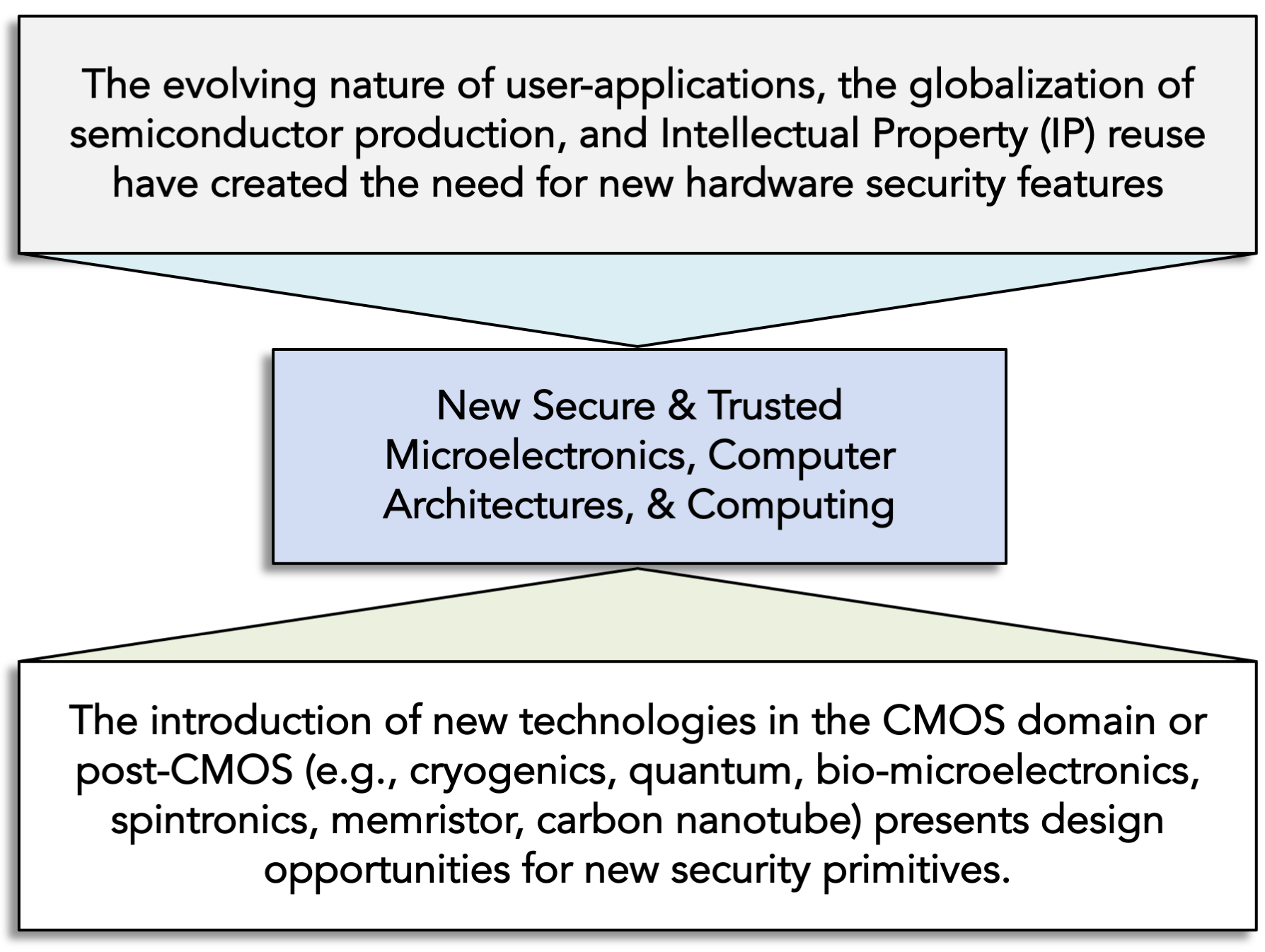
The two forces driving the need and innovation in the field of secure and trusted microelectronics, or simply hardware security, are the evolving nature of user-applications with greater security and privacy and edge computation, and the introduction of new devices that can be leverage to reinforce the security posture of microelectronics and to provide better security anchor to the whole computing infrastructure – hardware, firmware, and software. The center laboratories and research activities are organized to integrate these two forces.
Current Projects
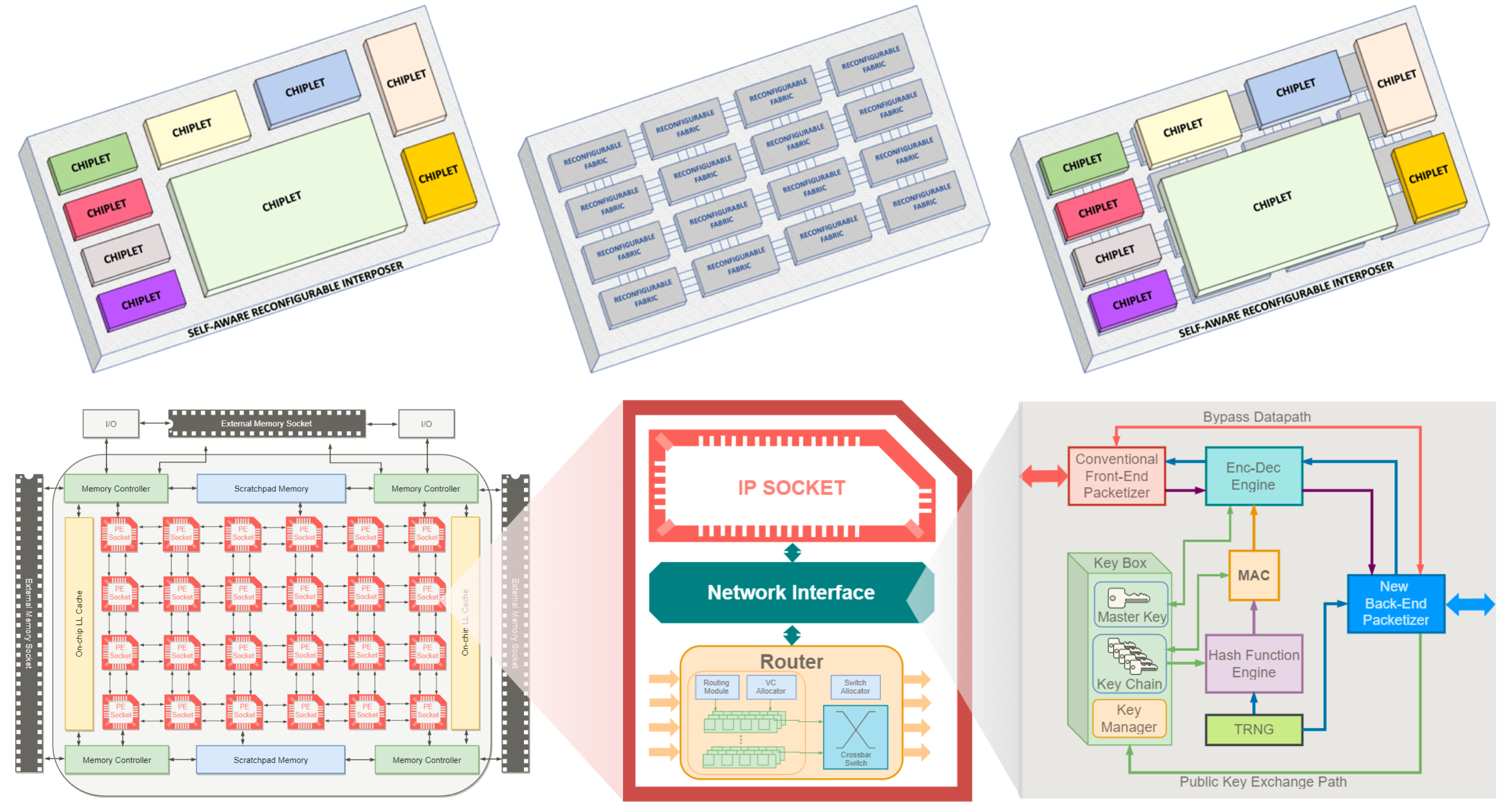
Using Security-Aware Reconfigurable Interposers: A new active interposer 2.5-D design methodology using reconfigurable logic targeting security applications. We imbue the active interposer with reconfigurable fabric that can be programmed at integration and end-use stages to provide hardware root-of-trust security guarantees.
Zero-Trust SoC Design: Building Secure System-on-Chip Designs from Untrusted Components
On SoC platforms consisting of multiple or a multitude of processing elements, the runtime interactions between processing elements can be very complex and difficult to fully analyze at design time.
The key innovation of the approach is that security is provided through (i) hardware virtualization that is completely independent of the processing elements themselves, and (ii) runtime establishment of trust among the elements.
The approach aims to reduce the system’s attack surface by creating a virtualization layer that isolates compute threads based on system and user-defined trust levels and security policies.
This project contributes to the protection of electronics systems against Side Channel and Malicious Hardware attack classes.
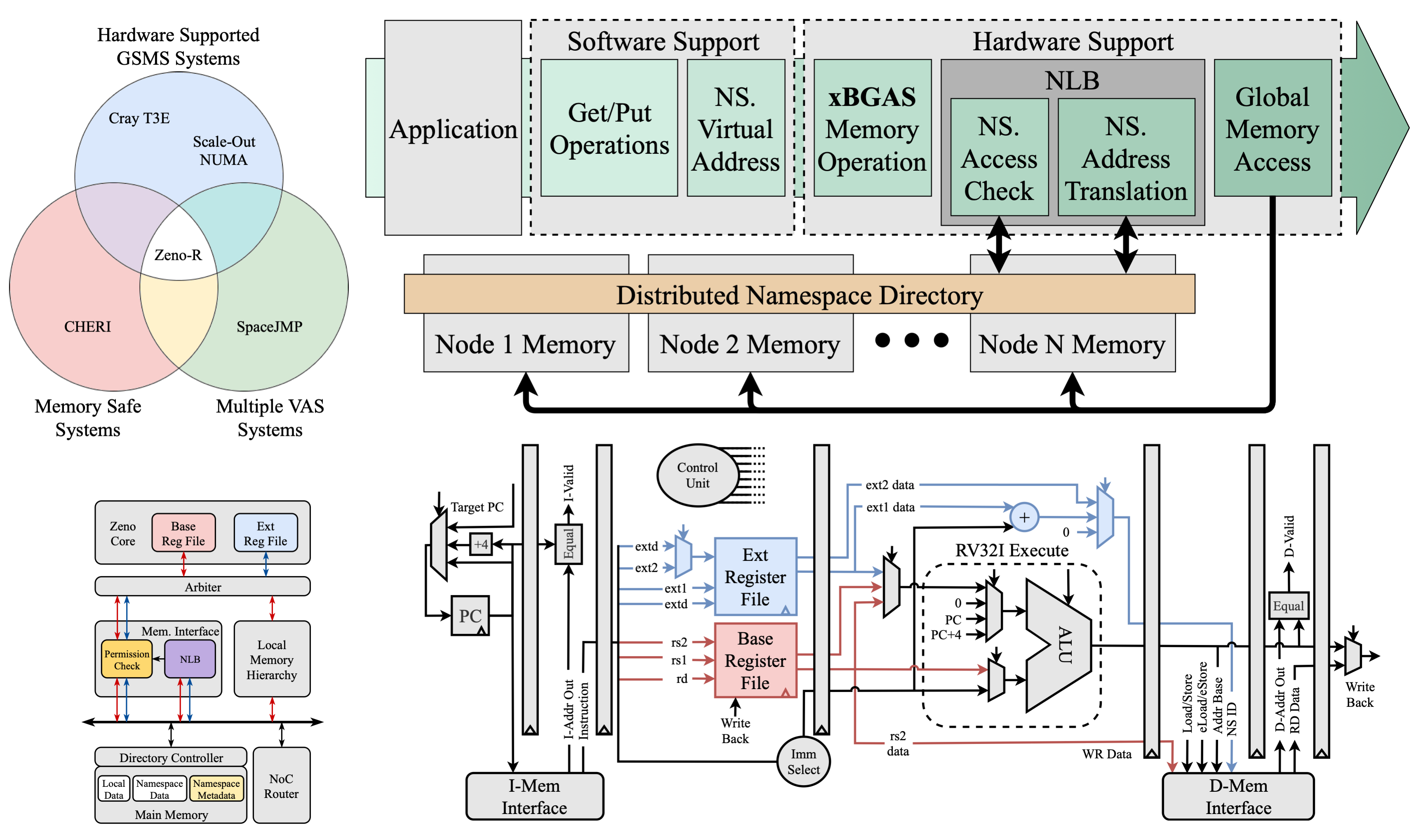
Hardware-assisted secure HPC/data-center scale shared memory: Zeno is a new security-aware scalable architecture for shared, distributed memory, high performance computing (HPC) systems. Its micro-architectural support for shared memory enables security-aware data sharing between different processors in a single HPC system without hindering scalability.
The Zeno architecture specifications, synthesized design, system support software, and programming tools will be open-sourced.
Zeno Architecture: A Secure High-Performance Computing RISC-V Processor Design
The traditional evolution of the HPC field has created an ecosystem where oftentimes a small number of systems would be commissioned by a government agency through a computer system vendor using (i) proprietary intellectual property (IP) blocks and (ii) obscure or rigid system architecture.
One can argue that the lack of open-architecture concepts in HPC and server-class systems has severely hindered innovation in the field. System-level security-related research efforts are generally altogether abandoned due to the lack of visibility or access to micro-architecture details to test, analyze or validate vulnerabilities, threats or risks.
Under this research effort, the team has introduced a new open-source server architecture, called Zeno, where high-performance and security are both first class system characteristics.
This project contributes to security and scalability of next-generation high-performance computing systems.
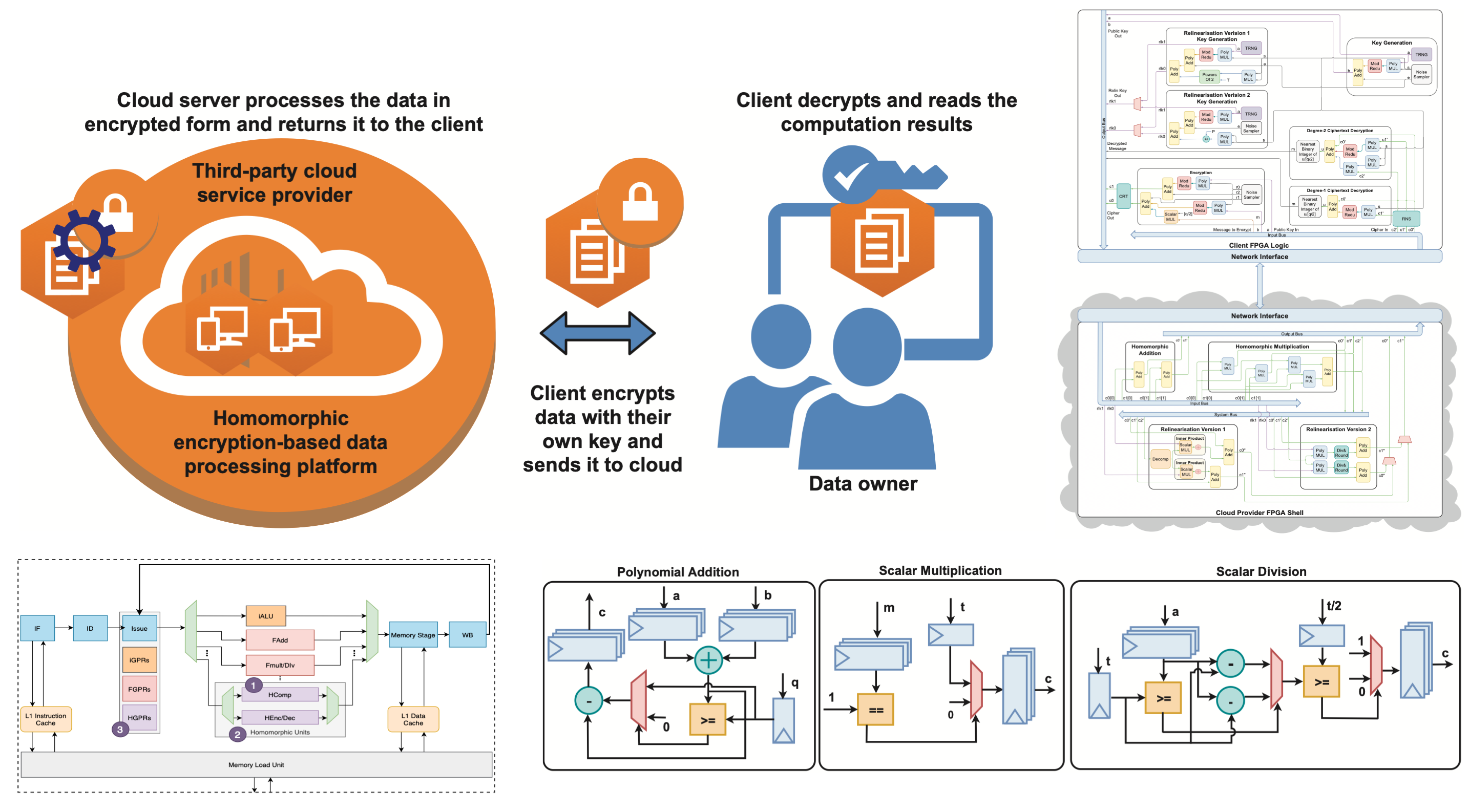
- Quantum-Proof Lightweight McEliece Cryptosystem Co-processor Design
- Fast Arithmetic Hardware Library For RLWE-Based Homomorphic Encryption
- A Post-Quantum Secure Discrete Gaussian Noise Sampler
- Open-Source FPGA Implementation of Post-Quantum Cryptographic Hardware Primitives
Homomorphic-Encryption Enabled RISC-V (HERISCV) Architecture
Large Arithmetic Word Size (LAWS): Word size directly relates to the signal-to-noise ratio (SNR) of how a ciphertext is stored and manipulated in computation. There currently is no hardware architecture that natively supports the register sizes and/or the execution units performing the fundamental mathematical and logical operations for lattice FHE schemes.
ISA Based Reconfigurable Architecture: Given the evolving state of improvements and new schemes in the field of FHE, the HERISCV architecture aims to provide an array of operations and functionality instead of optimizing the hardware for one particular algorithm. The architecture provides significant performance gains for lattice-based FHE applications as well as the flexibility to experiment with new designs by having instruction support for the core operations, e.g., lattices, polynomials, arithmetic, logic and finite fields.
This project advances our ability to perform secure and privacy-preserving computation at scale.
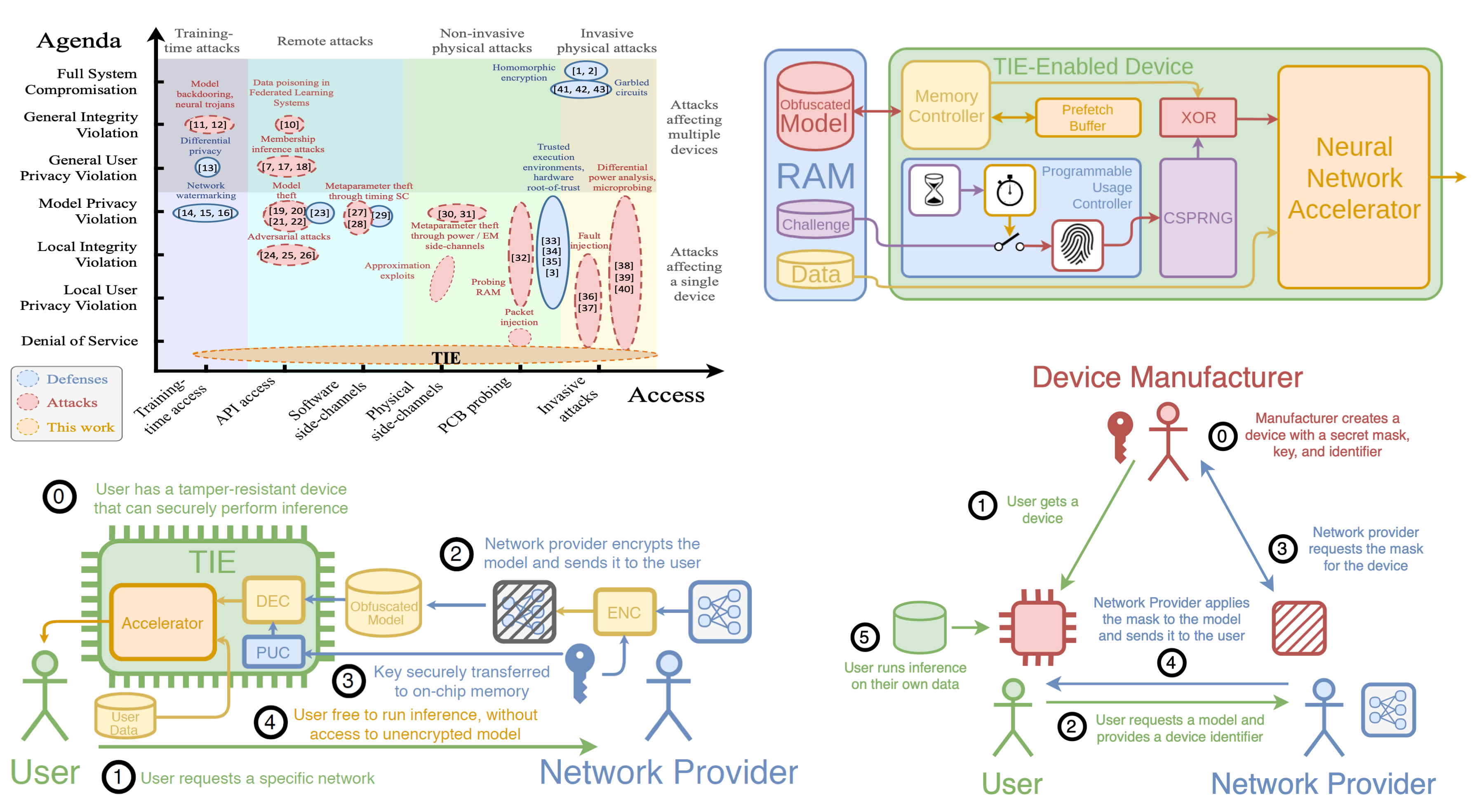
The team is developing algorithms, protocols and hardware solutions that allow designers to securely distribute their models without the risk of exfiltration. Our Trusted Inference Engine (TIE) architecture protects non-volatile memory against probing attacks and prevents API-based extraction by ensuring rate-limiting operations. Using our cryptographically secure anonymous authentication protocol, it fulfills the desired functionality for authentication and privacy while providing strong security guarantees for edge deployments.
Trustworthy And Privacy-Preserving Machine Learning Systems
Companies, in their push to incorporate artificial intelligence – in particular, machine learning – into their Internet of Things (IoT), system-on-chip (SoC), and automotive applications, will have to address a number of design challenges related to the secure deployment of artificial intelligence learning models and techniques.
Securing Execution of Neural Network Models on Edge Devices
Neural network model deployment in the cloud may not be feasible or effective in many cases. If the application requires near instantaneous inference and cannot tolerate the round trip latency associated with calls to a remote cloud server, then edge computation is often the only viable solution. The models are often trained using private datasets that are very expensive to collect, or highly sensitive, using large amounts of computing power. They are commonly exposed either through online APIs, or used in hardware devices deployed in the field or given to the end users. This gives incentives to adversaries to attempt to steal these ML models as a proxy for gathering datasets.
This project advances our ability to securely deploy machine learning applications with privacy-preserving guarantees.
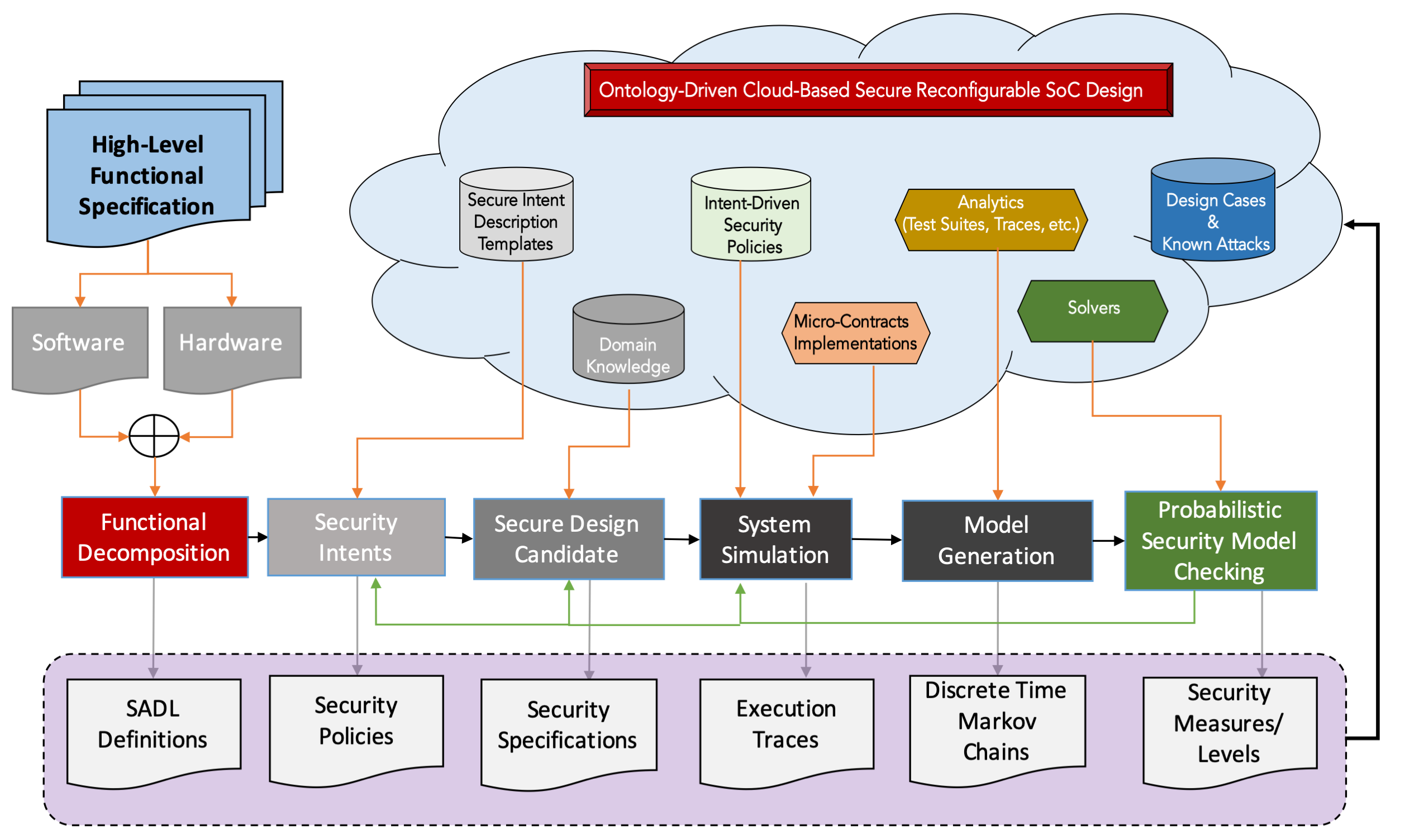
SODA Platform enables (i) continuous data collection on old and emerging attack tactics/models and vulnerabilities and (ii) application of machine learning algorithms develop or propose new protective design patterns with cost benefit analysis. Its aims to close the persistent semantic gaps that we observe across the different abstraction levels of the implementation by adopting a systematic and formal methodology that provably makes security policy guarantees across architectural abstraction levels – for this purpose, we are introducing the concept of micro-contracts.
SODA: Security Intent-Aware Ontology-Driven Architecture Design Platform
With the ever-increasing complexity of current SoCs, ad-hoc or independent security policy definitions or implementations have become unworkable. Considering security policies in isolation undoubtedly leads to lower risk assessment coverage, side-effects and composition inconsistencies.
The notions of security and secure system design are highly contextual. Therefore, their specification, interpretation, implementation and evaluation need to also be context based. Under this research effort, we use (1) user or designer defined security intents, (2) crowd-sourced or curated aggregated domain knowledge and expertise, and (3) machine learning enabled automatic security policy implementation composition to drive next-generation secure reconfigurable SoC design flow.
This project will significantly improve the nation’s microelectronic security posture.
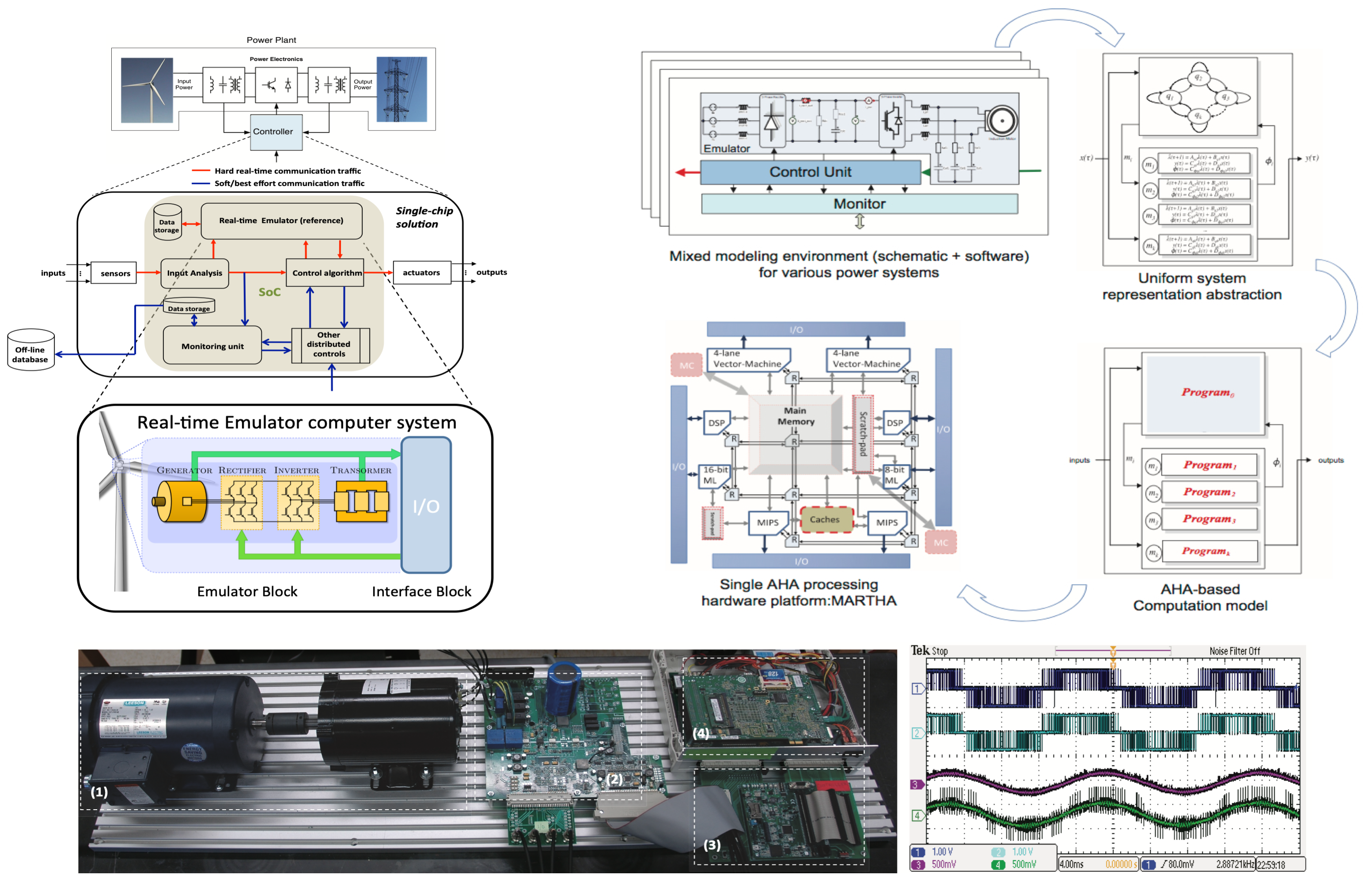
High-fidelity emulator of variable speed induction motor drive application: (1) Variable speed converter connected to a three-phase induction machine, (2) Inverter, (3) Controller and Real-time emulator.
As part of this research effort, the team has introduced the concept of Adaptive Hybrid Automaton (AHA) in modeling power systems as distributed cyber-physical systems.
EDA tool for Designing Secure and Resilient Power Electronics Systems
Researchers at the center are developing and deploying a novel software-hardware digital tool for design and testing of future power electronics enabled renewables integrated into the smart grid. The toolset is among the world’s fastest real-time digital emulator platforms for power electronics systems. The platform consists of a new multicore high-throughput low-latency processor architecture and new hybrid system simulation algorithms.
The tool mitigates some of the current limitations and bridges the gap between software simulation and real operation conditions, while taking high-power equipment out of the testing environment with minimal loss of fidelity. It helps to drastically reduce accidents during system testing and the risks of discovering an error in the very last stage of in-the-field testing and assembling after fabrication, and wide security and resilience ranges can be examined.
This project helps improve the security, resilience, and performance our power grid systems.
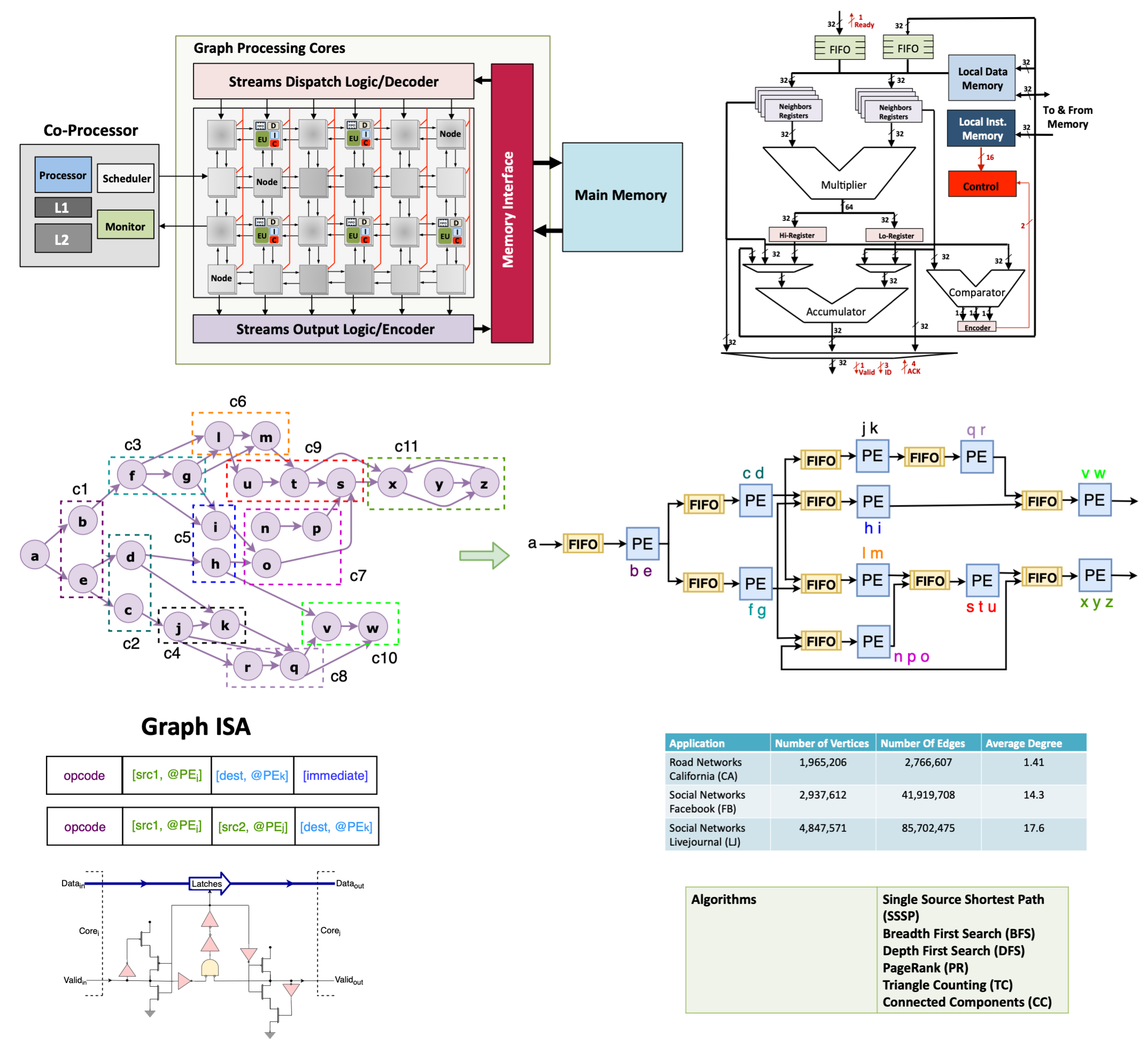
The application compilation and mapping process uses a graph clustering algorithm to optimize parallel computing of graph operations and load balancing.
High-Performance Asynchronous Graph Processor
Graph algorithms and techniques are increasingly used in scientific and commercial applications to express relations and explore large data sets.
In this work, we propose and design a new architecture, called Plexus, for the fast processing of large graph applications. To leverage the lack of the spatial and temporal localities in these applications and to support scalable computational models, we design the architecture around two key concepts.
The architecture is a multicore processor of independently clocked processing elements. These elements communicate in a self-timed manner and use handshaking to perform synchronization, communication, and sequencing of operations. By being asynchronous, the operating speed at each processing element is determined by actual local latencies rather than global worst-case latencies. We experience with a specialized ISA to support these operations.
This project advances faster data analytics.
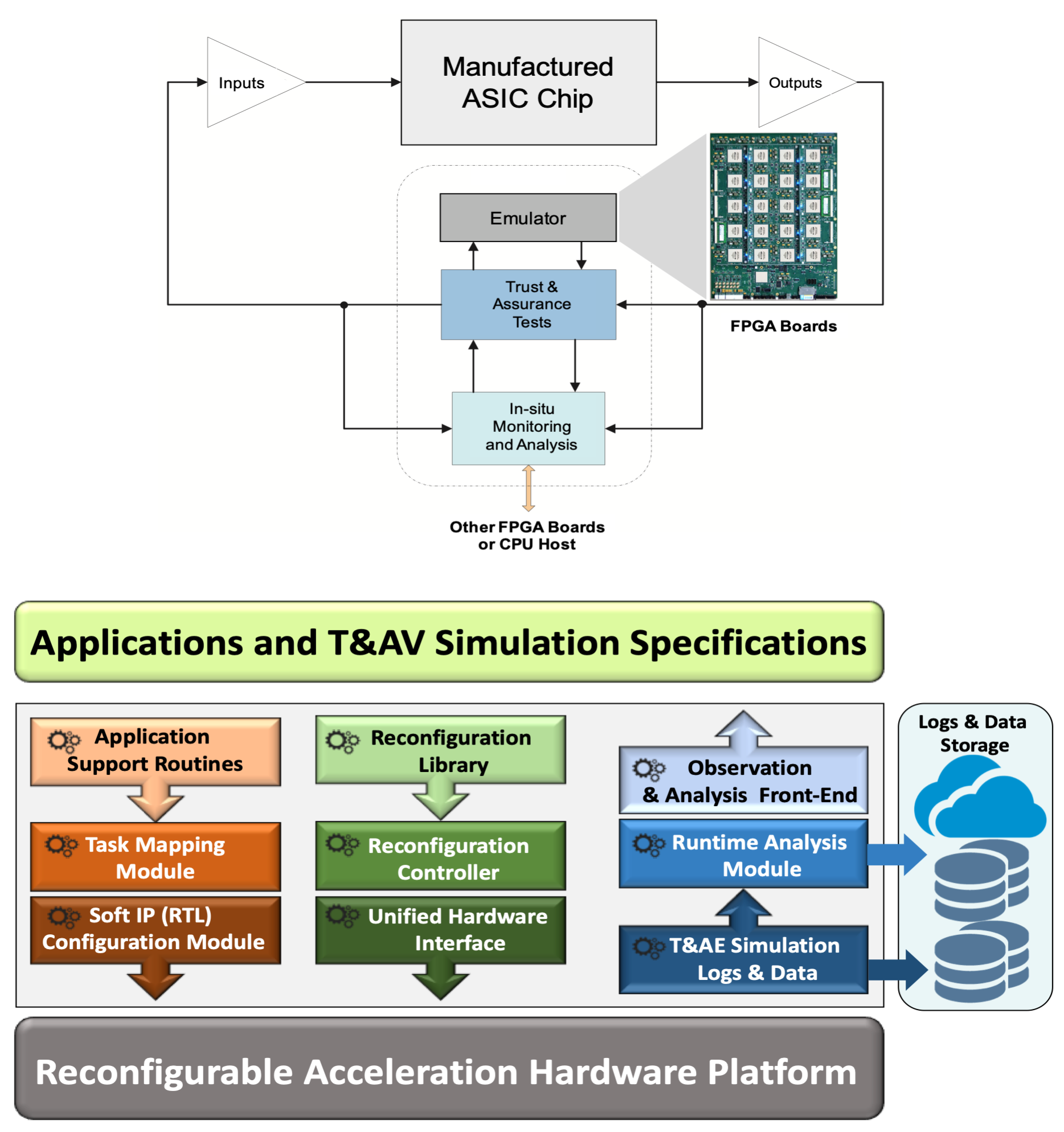
eTAVA: Trustworthy and Assurance Validation and Analysis of security ICs
To perform counterfeit chips analysis, to mitigate chip failure in mission-critical applications – defibrillators, pacemakers, and automotive and to assess the impact of counterfeit chips in medical devices and military applications, the team has introduced eTAVA (Emulation-based Trustworthy and Assurance Validation and Analysis) Tool is a software/hardware co-design platform for FPGA-based acceleration of trustworthy and assurance estimation and validation of IC designs.
eTAVA can be used in two modalities (1) to estimate and optimize the trustworthy and assurance properties of an ASIC design before manufacturing through simulation and analysis, and (2) to perform post-fabrication validation of these properties in a hardware-in-the-loop setting – the hardware here being an FPGA emulated version of the design.
This project advances methods and technologies for designing trustworthy and zero-trust secure electronics.
Current Tape-Out Efforts
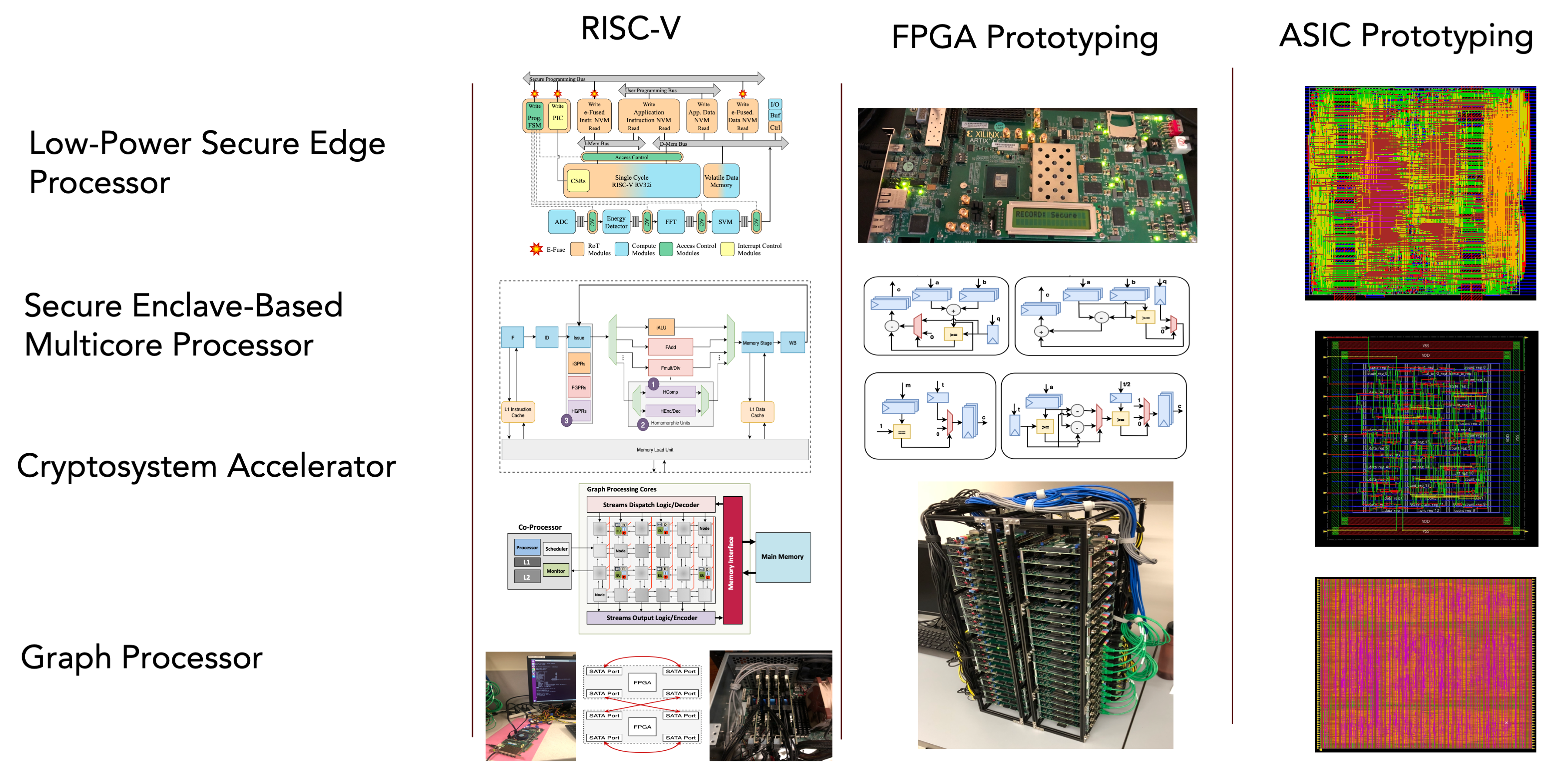
Translational Research Through Full-System Design
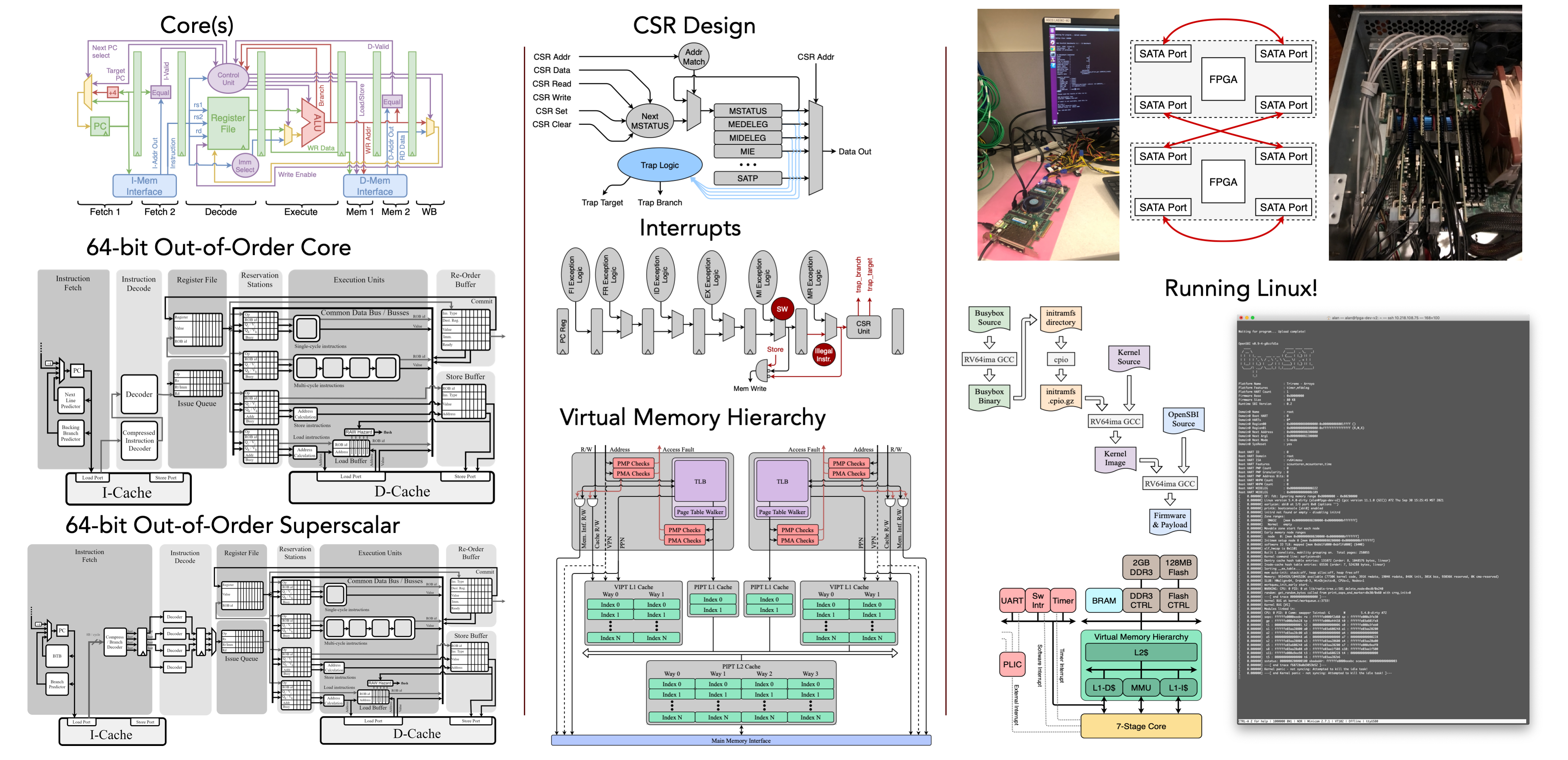
The center investigates, designs and prototypes secure full-stack computer systems using hardware-as-root-of-trust techniques and applied cryptography.
We apply an integrative approach consisting of algorithmic optimization, design flow automation, hardware-firmware co-development and prototyping.
We examine and design for (i) the security of the processing elements – data in transformation, (ii) the security of the communication among the processing elements – data in motion, and (iii) the security of the data storage and sharing – data at rest.